10. February 2021 By Arman Kohli
Measuring performance against (or just through) security costs
For many companies, focusing on their customers, expanding their services and improving the range of services they offer are key. This should support and optimise business processes to the greatest extent possible. In IT, IT service management (ITSM) is mainly concerned with optimising the quality of IT services. The focus here is on efficiency, process quality and the economic efficiency of IT services, thus paving the way for customer service to take front and centre.
These approaches can also be applied to information security to create greater transparency as well as make structures, areas of responsibilities and performance measurement clearer.
ITIL, one of the most widespread frameworks in IT service management, can be used. ITIL 4 offers companies a number of starting points in its latest publication. As part of this, ITIL factors in account recent trends, 34 different practices and seven principles.
Service orientation in information security
The acronym ITIL stands for Information Technology Infrastructure Library and was first published by the Central Computer and Telecommunication Agency (CCTA) in 1986. The core idea behind ITIL was to describe best practices for IT management.
ITIL V2 was published in 2000. ITIL V2 saw the related processes in the 42 books in V1 merged, reducing their number to eight. ITIL V2 emphasised the importance of a close relationship between customers, IT service providers and suppliers. This resulted in a more service-oriented approach. ITIL V3 was published in 2007 and had a service life cycle approach. Service delivery was seen as a continuous process, with new services being launched, continuously adapted and other services being decommissioned. The latest version of ITIL was published by Axelos in February 2019 under the name ITIL 4. ITIL 4 picks up on the latest technological developments and current trends such as agile approaches. This means that ITIL 4 provides a flexible basis for organisations on their path to digital transformation. The service life cycle and 26 service life cycle processes from ITIL V3 have been removed in ITIL 4. The idea behind this is to give service providers more leeway to define customised processes that meet the specific needs of the organisation.
The key concepts of ITIL 4 are the idea of value creation, the focus on value streams and the holistic view through the four dimensions.
The service value system contains the service value chain and takes into account the external influencing factors or requirements. The input is the demand of the customer, and the output is the goal or the value for the customer.
Information security costs
Reports of security breaches, attacks by cybercriminals and privacy concerns roll in almost daily. In March 2020, the English-language journal Bleeping Computer reported that hackers and cybercriminals around the world are using the coronavirus to launch an increasing number of phishing campaigns and cyber attacks. Theft of access data has also increasingly come to the fore, as has the distribution of malware. Information security, IT security and cyber security are of the utmost importance in times when both personal and professional circumstances can change at short notice, such as employees being encouraged to work from home, because, among other things, the potential and scope for damage is vast.
The result is that – in addition to current events that affect the entire world such as the Covid-19 pandemic – the spotlight has now also fallen on everyday issues, the use of learning platforms and the installation of new and/or other IT products, which hackers and cybercriminals exploit to cause damage and illegally obtain information. Temporary requirements or changes in the law also lead to additional expenditure or to the increased use of IT products for institutions that are not familiar with IT.
While it’s often possible for large companies to make whole teams or departments of employees available to ensure that information systems operate securely and to deal with IT attacks, smaller and medium-sized companies cannot always do this to the same extent. In addition to considering the cost aspect, companies also want support for their core processes, reduced lead times and to create control mechanisms and transparency across their entire in-house IT infrastructure.
A number of standards, policies and guidelines have been created to defend companies against the dangers posed by cyber attacks that are designed to help them integrate information security into their operations. The internationally recognised ISO 2700x series of standards is well-known in the information security world. These types of standards are designed to serve as a guide for companies, but don’t set out concrete processes or recommendations for action.
Processes in an ISMS
Following the ISO standard from the 2700x series as well as the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, BSI) standard, an ISMS can be characterised as the sum of processes, responsibilities, procedures, methods as well as resources, tools and a suitable organisational structure to enable management to comprehensibly control and document all activities and tasks oriented towards information security.
In practice, the implementation, operation, monitoring, review, maintenance and continuous improvement of information security are often neglected.
The primary objective of an ISMS is to protect all of a company’s data and information adequately, effectively and consistently throughout its entire life cycle against each of the threats that have been identified to ensure an appropriate level of security with regard to confidentiality, integrity and availability.
The process-oriented approach based on Deming’s PDCA model implements a continuous improvement process and leads to a learning organisation as a result. The same model is also used in numerous other ISO standards.
The PDCA model in ISMS includes the steps plan, do, check and act.
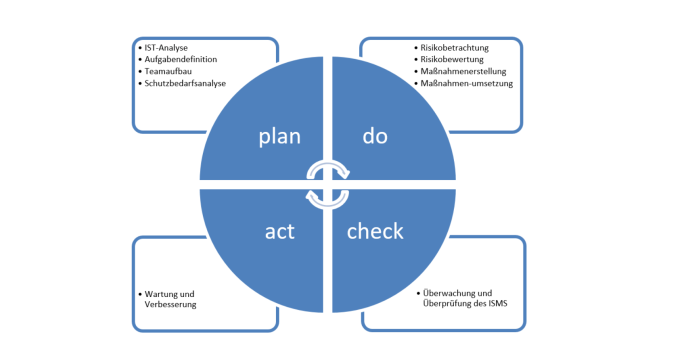
The plan phase includes identifying improvement potentials, analysing the current state and planning a new concept. The phase do includes the plans that have been drawn up, which are tested and optimised from a practical point of view. Individual tests are performed that should not influence the actual process for the time being. The tests that have been performed are examined and evaluated in the check phase. An improvement review will be conducted. If the improvement is successful, it will be implemented. In the last phase (act) the released state is implemented across the organisation. A periodic compliance review should be established. The improvement from the act phase is then followed by the next planning phase.
This is how defined key performance indicators (KPIs) can contribute to measuring performance in measurable processes. Risks that are identified and analysed can, for example, illustrate added value in a report together with measures. Identified risks that don’t materialise, but were communicated and analysed in advance, can even be presented to the management of a company as a success in relation to costs incurred.
Added value for companies
IBM’s Cyber Resilience Report, which involved more than 3,400 independent security researchers from the Ponemon Institute, also pointed to several vulnerabilities in IT organisations. The study examined the robustness of companies in the face of attacks. The result of IBM’s Cyber Resilience Report Study showed that only 26 per cent of the companies surveyed have a company-wide emergency plan. Of these, just under 30 per cent have concrete guidelines or processes on how to deal with typical attack methods such as DDoS attacks or ransomware attacks. The discovery that approximately 53 per cent of the organisations surveyed have experienced a significant data theft attack and approximately 51 per cent have experienced a significant business disruption in the last two years is also alarming.
Of the companies surveyed in the study, 74 per cent believe they made progress in the crisis management of cyber attacks. Just under half of them said they were able to contain attacks more quickly. Companies that didn’t make progress in this area attributed this to the loss of competent employees and an insufficient (security) budget first and foremost!
There is also a growing trend towards more artificial intelligence (AI) across industries and sectors. In terms of information security, while AI can help detect and combat attacks in an automated way, it can also be misused as an attack tool itself.
IT security researchers and security experts are showing how dangerous pure automation can be with increasing regularity. That’s why ITIL practices such as Continual Improvement, Knowledge Management, Monitoring and Performance are becoming increasingly relevant and companies’ trust in service providers offering AI products is becoming more and more important.
The possible interplay
ITSM and information security are different, but can work together well. Information can be used securely and customer satisfaction can increase as
- The service concept is implemented.
- Customers have more confidence.
- IT is focused on customer value and is more proactive.
- There is a shorter time-to-market.
Plus, response times can be shortened and the customer’s effort can be reduced. This is only a small selection of the benefits that can be unlocked by combining the two areas.
A focus on processes and value streams is essential for organisations in addition to placing a greater emphasis on service. The methods of attack and the challenges in the field of information security will continue to increase. It is therefore important to be aware of this and to act accordingly. Organisations should be constantly learning so as to continuously improve. Looking at the system as a whole is just as critical as being able to see individual processes in detail.
Practice has shown that optimising security management is often more effective at improving information security in the longer term than investing in security technology is.
The focus on ITSM in the IT environment is increasing. Improvements in security are becoming increasingly important as industries and sectors can also be affected by this issue in the short term. Everyone who uses IT makes themselves vulnerable and should take appropriate precautions. Statutory duty provides the framework, but standards and combinations beyond the standards can create better, safer and more cost-effective systems.
Added value becomes visible once you define performance criteria. Process, service and customer orientation are just as vital as using modern management methods. The standard can be significantly enhanced by taking a holistic approach with the four-dimension model, focusing on added value from the customer’s point of view, increasing the quality of work and optimising capacity through the basic principles and practices.
Would you like to learn more about exciting topics from the world of adesso? Then check out our latest blog posts.

